Estimado/a,
Quisiera por favor me puedan ayudar con estas 3 vulnerabilidades que se encontraron en el OJS 2.4.8.5 que manejamos en nuestra revista.
Ojalá puedan apoyarme,
Muchas gracias
Hello @ltenorio,
Sorry - but I will only be able to reply in English. The version of OJS that you’re using is no longer maintained or supported by PKP. I recommend that you upgrade to the newest version of OJS.
You may find the following resources helpful in preparing for and performing the upgrade:
These resources will introduce you to OJS 3 and how it is different from OJS 2:
If you are interested in professional, specialized support for your OJS install, including free upgrades, PKP Publishing Services offers a fee-based service which provides the hosting of OJS, daily backups of your data, applying security patches and upgrades, and priority answering your support questions. They offer solutions for a range of publishers, from small, cost-conscious or society publishers to full university and commercial publishing institutions. More information is available on their website.
Best regards,
Roger
PKP Team
Buenas tardes,
Si se esta pensando en migrar, pero mas adelante. No habrá alguna otra solución para la vulnerabilidad que describi?.
Muchas gracias,
Hola @ltenorio,
The first question (regarding XSS) isn’t clear – can you review the post and use the post formatting tools to format it clearly?
Regarding the second issue (an unexpected malicious hostname showing up in links) this could be caused by many different things and I’d need more information to make a specific recommendation.
Regarding CSRF protection, OJS 2.x does not offer this kind of protection and it would be labour-intensive to add it. I’d recommend upgrading to OJS 3.x to resolve this aspect.
Regards,
Alec Smecher
Public Knowledge Project Team
Buenas tardes, envío una imagen con la vulnerabilidad reportada:
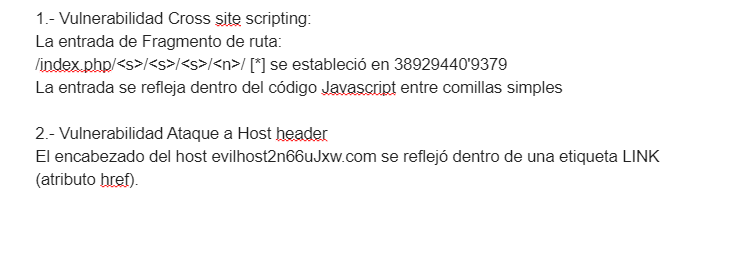
Muchas gracias por su respuesta,
Hola @ltenorio,
Lastimosamente eso no me da informacion suficiente para identificar ambas problemas. Si podes prestar mas detalles, es posible que pueda ayudar.
Gracias,
Alec Smecher
Public Knowledge Project Team
This topic was automatically closed after 6 days. New replies are no longer allowed.
