Hello PKP team and community,
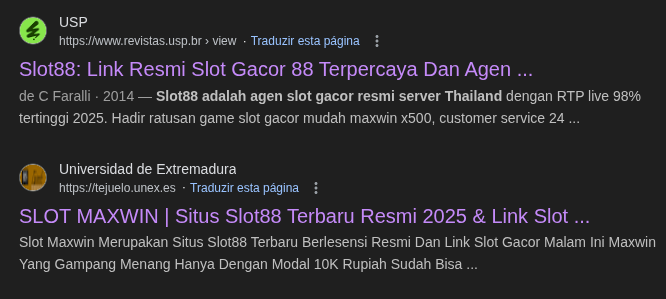
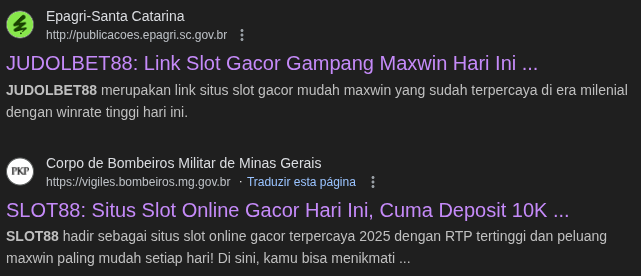
I am currently investigating what appears to be a coordinated cloaking attack affecting Open Journal Systems installations, where gambling content (e.g., Slot88 / Slot Gacor / Agen Slot) is being delivered only when the User-Agent is Googlebot.
This results in Google indexing and displaying gambling metadata instead of legitimate journal metadata, severely impacting the reputation and visibility of academic journals.
The issue is not visible to regular users or when accessing through a standard browser. The pages load normally in all normal browsing conditions. However, if the User-Agent is set to Googlebot, the response changes.
The behavior can be reproduced with:
curl -A “Googlebot” https://revistas.usp.br/
This returns gambling content, while:
returns the legitimate journal site.
This strongly suggests server-side cloaking, not spam submissions or editorial-side manipulation, and not simply page cache or metadata corruption.
At this point, it does not appear to be database-level spoofing, and I do not currently see evidence pointing to template or plugin modification, which raises concern that the vector may be external or injecting at runtime.
I have confirmed that this behavior is affecting multiple academic institutions running OJS, not just my installation. For example:
I also found a potentially related thread:
https://forum.pkp.sfu.ca/t/gambling-commercial-inside-php-library-used-by-ojs/97184/4
Why this is concerning
-
It appears to be a targeted attack on OJS infrastructure
-
It is Googlebot-only, so admins may not notice it
-
It causes SEO poisoning, blacklisting risk, and academic credibility damage
-
Multiple universities appear compromised in the same way
-
From early inspection, this seems like an external runtime injection / cloaking layer rather than editorial or database corruption
Request
Has the PKP team observed similar reports?
Are there any known vulnerabilities or guidance for detecting/removing cloaking payloads affecting OJS specifically?
I believe many administrators may be unaware because the site looks normal in browser tests — but Google is currently seeing an entirely different payload.
Regards,
Tarcisio Pereira