Hi guys, im using OJS 3.2.1.1.
I have a problem with the OJS backend, the menu on the OJS backend can’t appear when i enter journals, it gets stuck and just keeps on loading.
I have tried to fix it by delete cache browser, clear data cache, clear template cache but nothing happen.
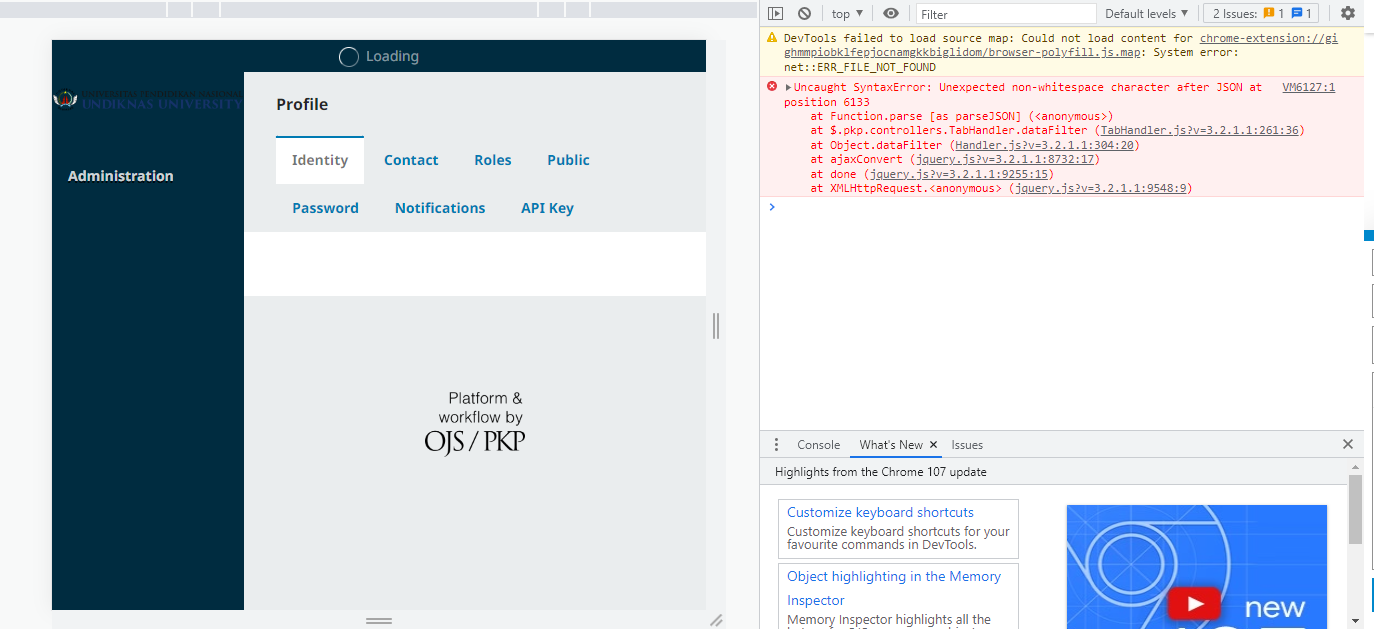
Any idea? pls help on how do i fix it…
Regards
Hello @im_destra
Have you do OJS upgrade recently ?
Best
Hendra
Hi
I did the upgrade OJS 2 years ago, and nothing happened. This issue appeared 2 days ago.
Hello @im_destra
Can you check the error log on your server for the domain that used by the OJS?
And paste the related error here so the community can help you with that.
Regards
Hendra
Hi
i have turn on display_errors setting in config.inc.php, and this error appear when i login on user menu dashboard.
method PKPApplication::getRequest() should not be called statically in xxx/plugins/generic/registrationNotification/RegistrationNotificationPlugin.inc.php on line 54
Warning : Cannot modify header information - headers already sent by (output started at xxx/plugins/generic/registrationNotification/RegistrationNotificationPlugin.inc.php:54) in xxx/lib/pkp/classes/template/PKPTemplateManager.inc.php on line 915
Warning : Cannot modify header information - headers already sent by (output started at xxx/plugins/generic/registrationNotification/RegistrationNotificationPlugin.inc.php:54) in xxx/lib/pkp/classes/template/PKPTemplateManager.inc.php on line 916
hi
i’ve finish my issue, this is related to malware.
somebody is attach html code on my index.php.
can anyone tell how to secure my ojs data and avoid this problem occur again in future ?
thanks
regards
im_destra
Dear @im_destra
Here is my suggestion :
- Upgrade your OJS to the latest version
- Configure the base_dir on your PHP-FPM configuration for other vhost on your server so it won’t affect other vhost when one of the vhost get hacked
- Disabled the php function in php.ini “exec,passthru,shell_exec,system,proc_open,popen,curl_exec,curl_multi_exec,parse_ini_file,show_source”
- Add protection layer to your domain such as using cloudflare or ModSecurity
More of this can be read here :
https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi6o7jT0qL7AhXK-XMBHbjkBIYQFnoECBMQAw&url=https%3A%2F%2Fopenjournaltheme.com%2Fdocs%2Fhow-to-secure-ojs&usg=AOvVaw17GnVOJLbiyDyaynERfoCB
Regards
Hendra
1 Like
Hi @im_destra,
Was your files_dir (in config.inc.php) configured inside your web root? If so, that’s an unsafe misconfiguration, and the most common way OJS sites get attacked.
Regards,
Alec Smecher
Public Knowledge Project Team
1 Like
