Hi there,
My site: http://canadianoncologynursingjournal.com has been hacked, and I’m not sure how to fix it. Every single page has been replaced with the content shown in the picture.
My question is, how do I go about fixing the site? The database doesn’t seem to be affected, so is there any way to restore the site from that? The backups available have been overwritten with the hacked files.
The files folder is in the public_html folder, so I know I have to move that, but is there any way to recover the site without having to rebuild from scratch?
Thanks.
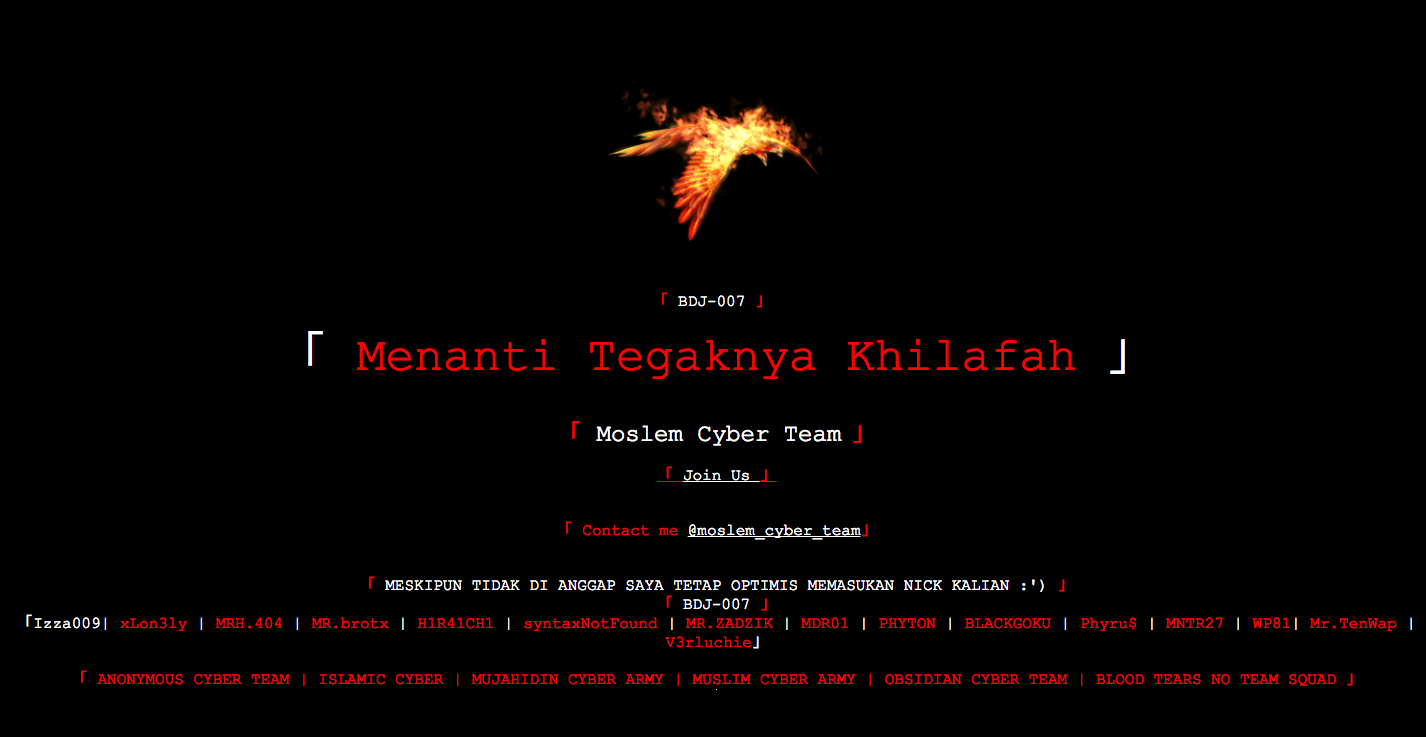
Hi @sherrikeller,
Was your files_dir a subdirectory of your web root? If so, that’s probably how your system was attacked. See PKP Applications and Security for some information on how to deploy our applications safely.
Once a server has been broken into, you should treat all content on it as suspect. If you didn’t make any changes to your OJS code, then I would suggest thoroughly reviewing the contents of the files and public directories, saving them (along with the database), and discarding the OJS code in favour of a fresh install from a new .tar.gz download.
Regards,
Alec Smecher
Public Knowledge Project Team
Yes, files was a subdirectory of the web root.
Is there a way of recovering submissions? or do I have to start from scratch again? I have no idea how to fix this.
So I reinstalled all of the OJS files, and have upgraded OJS.
I don’t know how to make my files folder not publically accessible. In another thread, this had been suggested: “We recommend placing the files directory outside of the web server’s root, or protecting it from direct access e.g. using an .htaccess file.”
I had used the .htaccess method on the website, but it appears that it was insufficient. How do I hide files properly?
Hi @sherrikeller,
What did you put in the .htaccess file? One way to test whether it’s working is to try downloading a file directly from the files directory by constructing its URL. Generally, if you’re able to access or download the file, it’s not safely protected.
The safest way is to keep the files_dir outside your web root. On most servers your web root will be called something like www or htdocs. You’d just have to make sure the files_dir was placed outside of these two directories. Details will vary by server.
Regards,
Alec Smecher
Public Knowledge Project Team
I think it said something like ‘deny from all’.
Should the files folder go in a subfolder of the public_html folder, or somewhere else?
Hi @sherrikeller,
No, the files_dir should go outside the public_html folder. Otherwise it risks direct access via the web server.
Regards,
Alec Smecher
Public Knowledge Project Team
ok, but I don’t know how to make a link to a folder that’s above in the public_html file though?
i tried /var/files, with /var/ being the same level as the /public_html/ but it doesn’t work
Hi @sherrikeller,
This will depend on your server setup and the level of permissions you have, so I’m afraid it’s difficult to make specific recommendations. I’d suggest asking your server administrator or hosting support.
Regards,
Alec Smecher
Public Knowledge Project Team
I have finally sorted out the configuration of the files folder and reuploaded all of the article files. Thanks for your help!
Now the problem I’m having is when I try to upload an image file for an announcement, it doesn’t work. When I click on Manage your uploaded images, I get the error “The directory specified for uploaded files does not exist or is not writable.”
Any idea how I should go about fixing that?
Hi @sherrikeller,
The most likely cause is a file permissions problem in your public directory or its subdirectories. The permissions here have the same requirements as for the files_dir I believe you’ve already been working with.
Regards,
Alec Smecher
Public Knowledge Project Team
Interestingly we have been hacked several times. Our files are inside the public folder. Moving them outside does not seem to help. But here is the interesting discovery. the username and password are in clear view in the config.inc.php file. Why is this necessary? If someone can break into this file they have access to everything on our server including directories outside OCS. I have not checked but I imagine that this is also true in OJS.
How on earth can this be changed and why is it necessary?
Thanks
Rick
I just checked OJS and it is also clearly there.
Hi @RickMath,
Including the DB password in a plaintext config file is standard practice. It’s normal to protect this file from access by others on the same server using file permissions. Many similar systems e.g. Drupal and Wordpress do the same.
It’s also good practice not to reuse credentials – your database credentials should not be the same as e.g. your CPanel or Journal Administrator credentials.
If you’ve been hacked before via your files_dir being public, the hacker may have left backdoor scripts in your server filesystem.
Regards,
Alec Smecher
Public Knowledge Project Team
Hi all! We are soliciting feedback and proposals for hacking claims via image uploads on this Github discussion. Feedback would be welcome.
Regards,
Alec Smecher
Public Knowledge Project Team
