We have had recurring problems of people/bots making accounts and then uploading junk files such as html or php files, most recently in January after which I upgraded to 3.3.0.13 from 3.3.0.6.
I delete these accounts and the associated junk files. I thought things were okay but the journal back end is now throwing errors, and the four tabs on the Submission page (My Queue, Unassigned, all Active, Archives) are all empty when they should not be, even though the Editorial Activity page correctly shows 23 active submissions.
The errors are:
- “Error. An unexpected error has occurred. Please reload the page and try again” as soon as I log in.
- “Failed Ajax request or invalid JSON returned” when I click on the notification bell.
The error log has this error multiple times “ojs2: 404 Not Found” but no actual PHP errors.
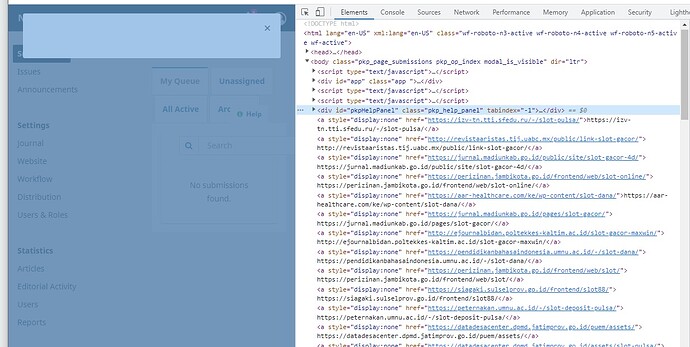
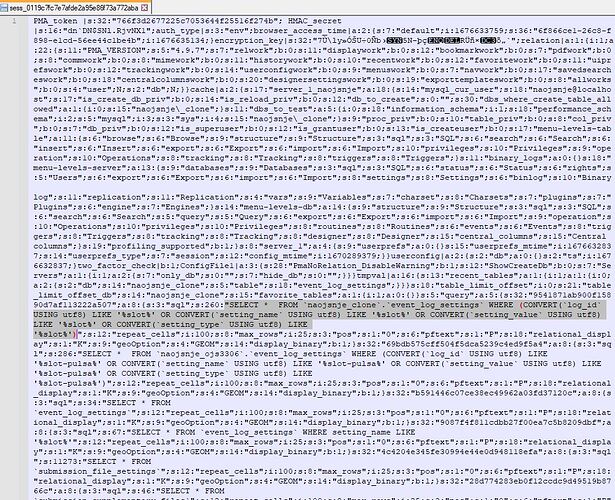
If I inspect the page when it shows an error, the div with the id pkpHelpPanel has a long list of hidden URLs of what look like hacked OJS journal sites (see screenshot) all containing the word “slot”. I’ve searched within my database and all files for this text. It seems the session files (e.g. sess_0119c7fc7e7afde2a95e86f73a772aba) in the tmp folder contain code to query the event_log (see screenshot) for files for which the original filename contained “slot”. I’ve deleted these records, and files, and the session files. However logging out and in again regenerates session files with this malicious code.
It seems to be a ‘task’ page that loads the list of hidden urls (/$$$call$$$/page/page/tasks?_=1676637218768).
Additionally, every page on my site has a list of hidden URLS at the very last line (below the closing tags) like this:
I don’t know where there malicious code is that is causing this, or how to get rid of it. As I said, I’ve searched within the databas and files. And how to get the submissions tabs to show the correct files. I have daily backups and could revert to a previous version but - without fixing the actual problem - I suspect the same problems will arise. Looking back at a copy of my 3.3.0.6 version I see that this problem was there too and therefore was not removed by the upgrading process.
This is obviously something which has affected many other sites (the list being displayed is long).
Sorry for the long post. I’ve spent a lot of time trying to work out what is going on and I’m not sure what else to try.
If anyone could assist at all, I’d be very, very grateful!